Hi everyone! In a previous post I’ve described how to enable the Kasten K10 Multi-Cluster Manager Using the Kasten UI which is available since v7.
One of the requirements to enable the Multi-Cluster Manager is using a secure connection (HTTPS) with a valid SSL certificate to connect with the Kasten UI Dashboard. But what if our connection doesn’t have proper SSL certificates? What if we are using HTTP instead of HTTPS? We will see how to enable this using the CLI.
NOTE: By all means, we always recommend to use a secure connection to connect with Kasten UI. This workaround should be used only for Lab or demo enviroments.
Pre-requisites
So, what do we need to enable Multi-Cluster Manager? Very simple:
- We need 1 Kubernetes cluster with Kasten already installed, which we will set as the Primery cluster in the Multi-Cluster Manager.
- 1 or more Kubernetes clusters with Kasten already installed, which we will set as Secondary clusters in the Multi-Cluster Manager.
- The Kasten’s ingress (it could be via Ingress, Load Balancer or an OpenShit Route) in the Primary Cluster must be accessible by all Secondary clusters.
- Secondary Dashboard Access via Multi-Cluster Dashboard (Optional)
- Secondary Cluster’s API Server must be accessible by the primary cluster.
- Secondary Cluster’s K10’s ingress must be accessible by the primary cluster.
Enabling the Multi-Cluster Manager in the Primary Cluster
We can enable the Multi-Cluster Manager in the Primary Cluster, just as we described in the previous post. To enable the Multi-Cluster Manager in the Primary Cluster, we need to connect to the Kasten UI for this Primary Cluster, and click in the Multi-Cluster section of the main menu.
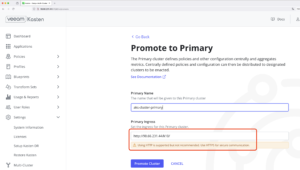
In the Multi-Cluster page, click in Promote to Primary
In the Promote to Primary Page, provide the following information:
- Primary Name: This is basically an alias for the Primary Cluster in the Multi-Cluster Manager
- Primary Ingress: This one provides the Ingress URL for the Kasten instance installed in the Primary Cluster, and it’s auto-filled by default.
- The required format for the URL is <URL of cluster>/<helm release name> (e.g., https://kastengkemc1.vlatam.net/k10/)
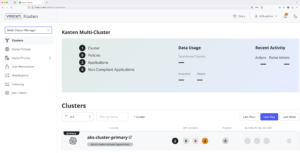
Once this process is completed, which usually takes just a couple of seconds, you will see that the Multi-Cluster Manager is already enabled, with just one cluster for now, the Primary Cluster:
Adding a Secondary Cluster to the Multi-Cluster Manager
Once the Primary Cluster is already configured to use the Multi-Cluster Manager, we can add Secondary Clusters. In order to do this, we need to complete the following steps:
Create a Join Token in the Primary Cluster
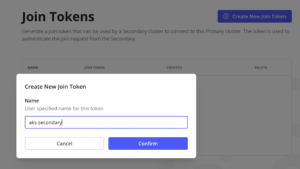
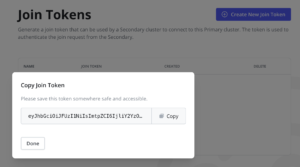
In order to add a Secondary Cluster to the Multi-Cluster Manager, first you need to create a join token in the Primary Cluster. This join token will be used by the Secondary Cluster to connect with the Primary Cluster. The join token secret can be created in the Kasten UI using the Multi-Cluster Manager Dashboard and cliking in Join Tokens:
Click in Create New Join Token and then provide a name for the token. This name will be the name of the Secret created in the Kubernetes cluster.
Click in Confirm and you will get the Join Token.
Joining the Secondary Cluster to the Multi-Cluster Primary Cluster
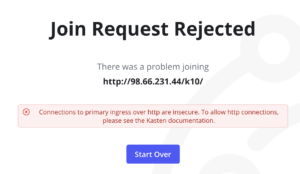
Now, if you try to follow the previous post, joining the Secondary Cluster to the Primary Cluster using the Kasten UI, at the moment you provide the Token, you will get the following error message.
This error is because we aren’t using a secure connection via HTTPS with a valid SSL certificate. In order to fix this error, we need to run the following command in the secondary cluster, so we can allow the Multi-Cluster configuration without a secure connection.
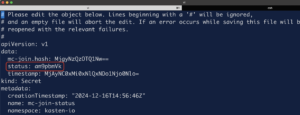
To verify that the Secondary Cluster has joined correctly to the Primary Cluster, run the following command using Kubectl in the secondary cluster to edit the secret called mc-join-status in the kasten-io namespace
In the data section, the status should be “am9pbmVk“, which is after being decoded means “joined“.
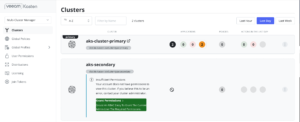
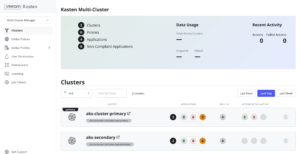
Now if we check the Kasten UI, we should see both clusters
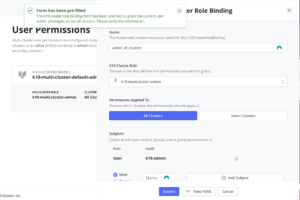
Of course, just as we explained in the previous post, it is necessary to assign proper privileges to get access to the secondary cluster by clicking in “Grant Permissions” in the green box.
Then it will be possible to manage BOTH clusters using the Multi-Cluster feature.
As you can see, even when we recommend always to use secure connection for Kasten, in case you aren’t able to have proper HTTPS connection, you still can enable Multi-Cluster feature using CLI.





Get Social